Using SSH
We have changed our policy for SSH
to better our security on all the servers. All clients have
been added an SSH icon in their Domain Manager. Via this addition
you will be able to enable SSH access to your account.
To setup an
RSA key follow the instructions below.
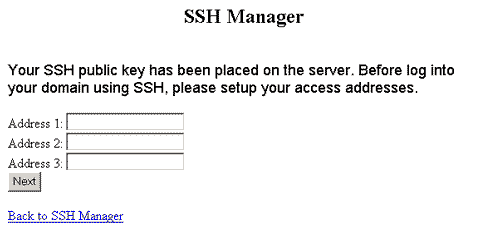
Please note that you do not have to
have a RSA to gain access. You can also leave the RSA field
blank, and it will take you to a second screen that will allow
you to put in where you are connecting from. (by IP address)
If you have a static IP, just enter the IP address that you
connect to the net with and hit submit. If you have a dial-up
and you have a different IP every time that you connect, just
put in the Class B that you connect with. Lets say that your
IP address right now is 65.123.43.23.
IP --> 65.123.43.23
Class A --> 65.*.*.*
Class B --> 65.123.*.*
Class A addresses will not be allowed
due to the number of IPs that can be connected from. So to
put in your Class B you would put "65.123.*.*" in the field.
But now lets say that you connect 3 different times and get
3 different Class B's, just put them all in.

Overview of
RSA Authentication
RSA authentication uses a public-private
key pair to authenticate and log in to an SSH1 Server. It
offers a higher level of authentication security than password
authentication by requiring both the private key and the passphrase
that protects the private key in order to complete authentication.
Setting up RSA Authentication for a
SecureCRT session is a multi-step process. Identity Files
are created with the RSA Key Generation Wizard. The identity
file is defined for global or session-specific use in the
Advanced SSH Options dialog. Then the public key is added
to the authorized_keys file located on the SSH server.
Note: Only SSH1 supports RSA authentication.
Creating Identity
Files
To create an RSA identity file:
Open SecureCRT and goto Options.
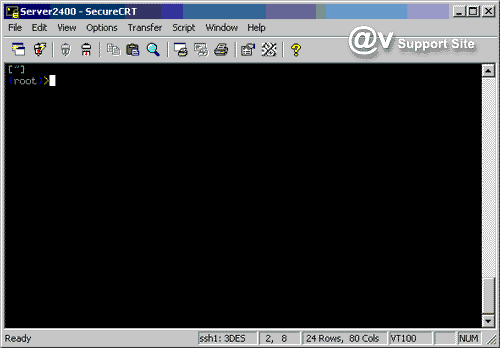
1. In the Connect dialog, select the
SSH1 session with which you would like to use the identity
files.
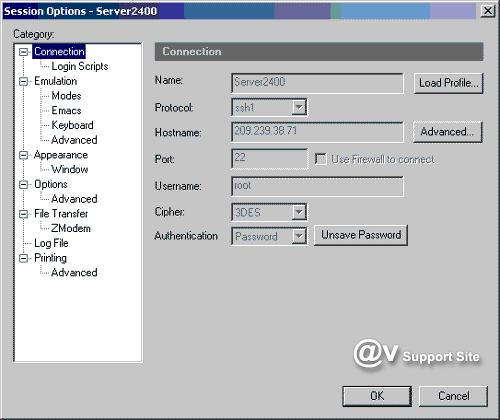
2. Open the Session Options dialog
and in the Connection category, click the Advanced button.
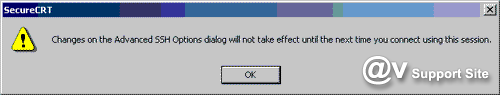
When Advanded is clicked, an alert
box is activated and states "Changes on the Advanced SSH
Options dialog will not take effect until the next time you
connect using this session."
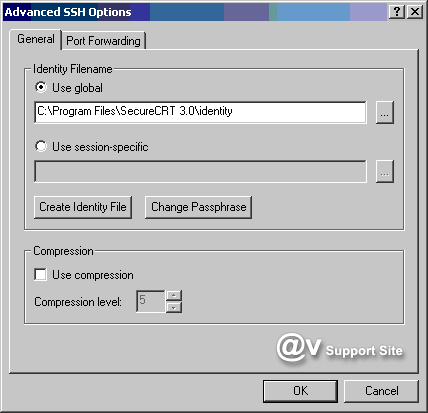
3. Select the General tab and click
on the Create Identity File button in the Identity Filename
section.
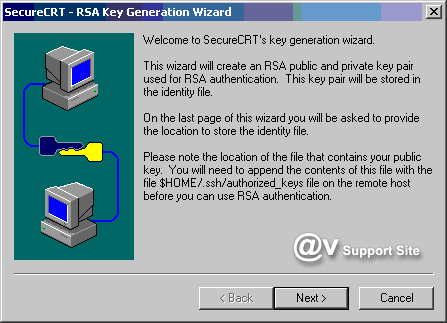
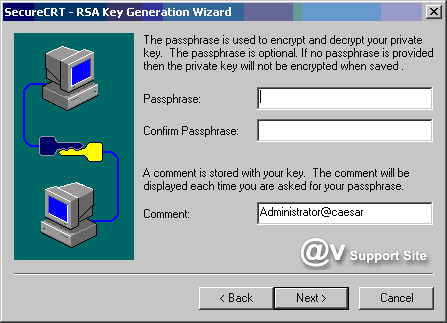
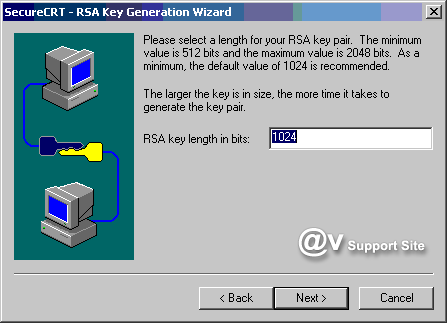
4. Follow the instructions in the RSA
Key Generation Wizard to create your identity files. Once
your public-private key pair has been generated by the RSA
Key Generation Wizard, you will be prompted for the path and
filename in which your private key will be stored. Be sure
to specify a secure location for this file such that you are
the only individual with access to it. The public key will
be placed in a file with the same basename as the private
key file, but with an extension of .pub.
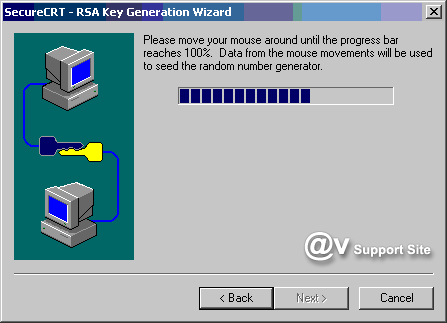
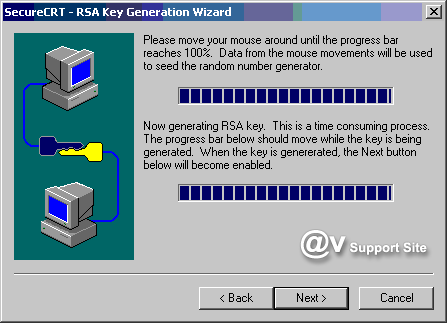
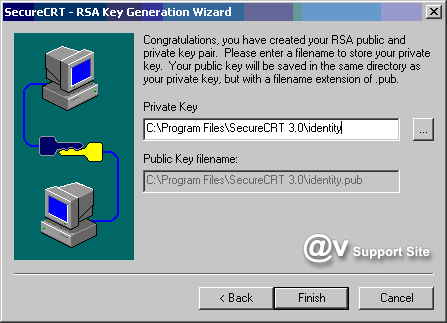
Once you have created the RSA key you
will need to open the file in a text editor and then copy
and paste it into the field that is provided in the first
screen of the SSH section in the Domain Manager.
Congratulations, you have created your
RSA public and private key pair.
|












